Password cracking is becoming very trivial with the vast amount of computing power readily available for anyone who desires so.
At a current rate of 25$ per hour, an AWS p3.16xlarge nets you a cracking power of 632GH/s (assuming we’re cracking NTLM hashes). This means we’re capable of trying a whopping 632.000.000.000 different password combinations per second!
Now, if we use this as our average crack speed, the table below shows how long it would take us to crack different kinds of passwords.
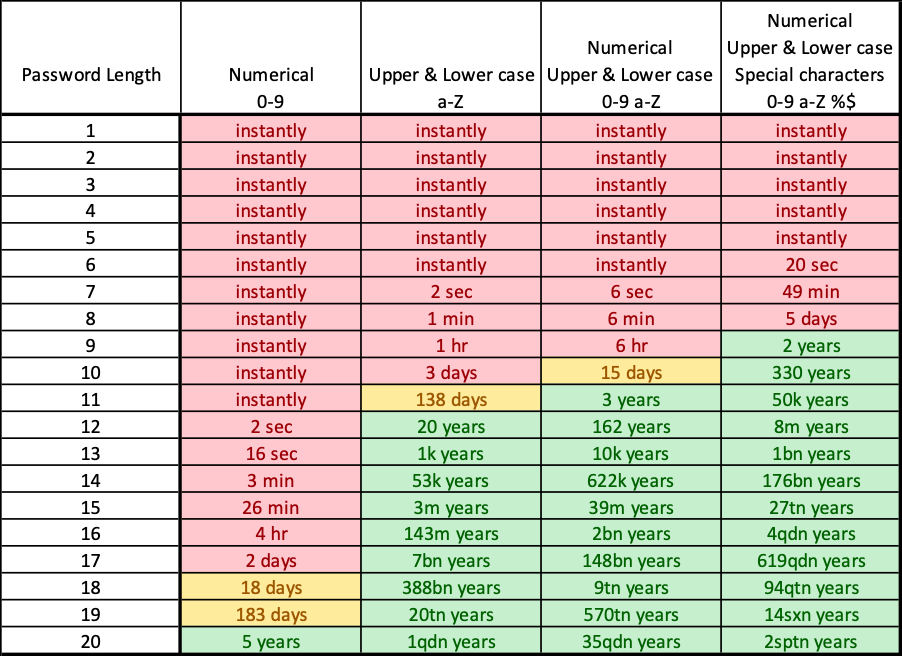
This means that if some attacker were to stumble over the NTLM hash of your super complex password of 7 characters, and that attacker has 1 hour and 25$ to spare… your password is cracked.
Add another character to your password, and suddenly, the attacker in our scenario would need a maximum of 5 days and 3000$ to crack your password (along with all other passwords with a length of 8 characters). If you keep adding characters, you see that the time needed to crack the password is growing exponentially.
So, the key takeaway here is basically: “the longer your password, the better”.
We strongly recommend using passwords with a minimum length of 10 characters (including numerical, lower & upper case, and special characters). If you have trouble remembering complex passwords, try using pass phrases or generate random passwords and store them in a password manager.

Sources: