At the Security Factory, we are constantly looking to improve the security of our customers. This time, we are upgrading our reporting technique. With a new online platform where customers can log in and evaluate the security of their applications in real-time while we are testing.
Previously, after a penetration test, our customers received a PDF report with all the information about the executed penetration test. This included scoping details, timeline, management summary and graphs, finding details with remediation advice, consequences and evidence etc.
Easy to say, this could be a very lengthy document for some tests where you could lose the overview of the complete test. But of course, this was how we delivered testing results for the last 10 years and it has been proven to work for many of our customers.
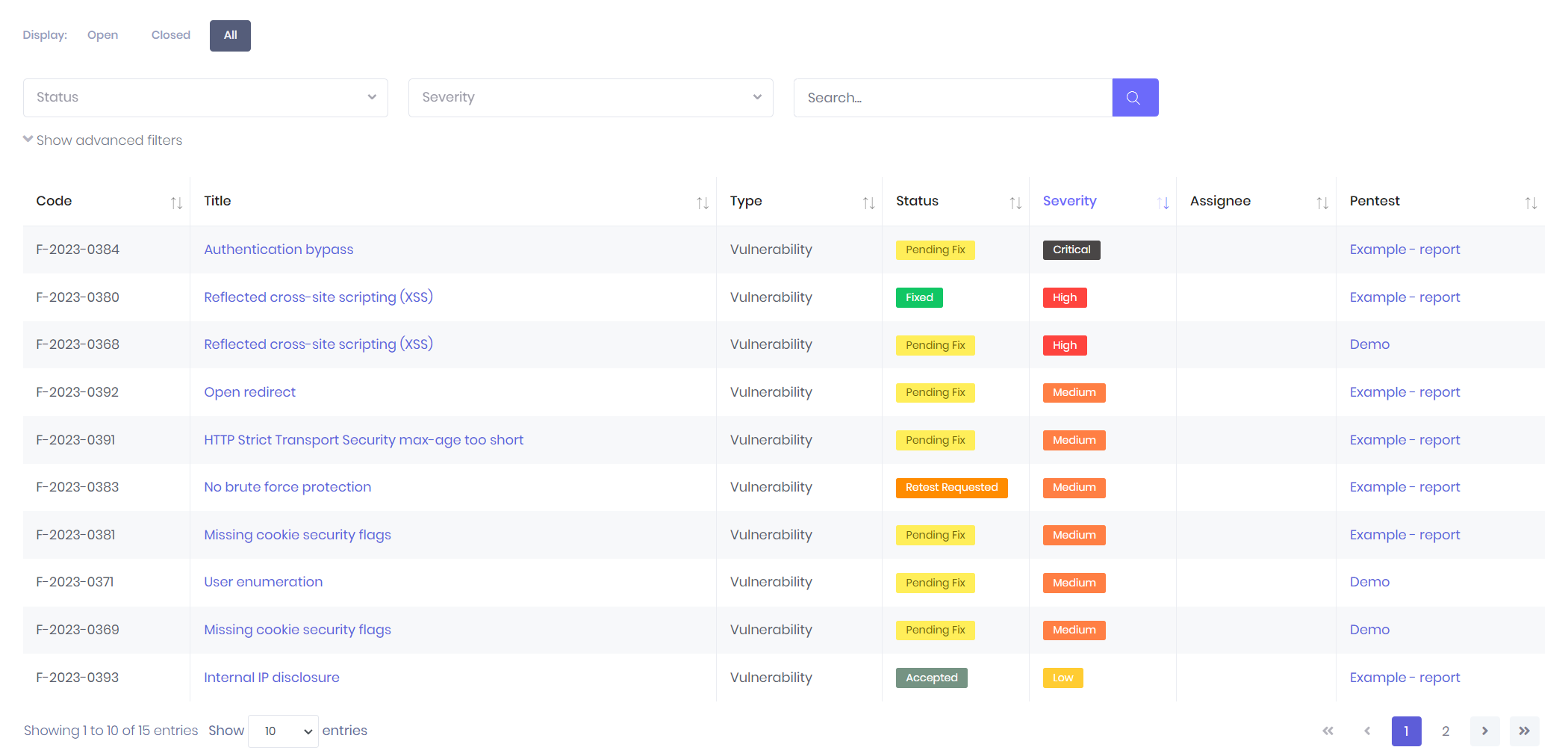
However, in today’s fast-paced business (and security) environment, a quicker way of delivering results is needed. With our new online reporting tool, we can deliver real-time updates and insights while testing the application. This way, all necessary information can be directly communicated with the correct people and security flaws can be fixed faster. It even provides an easy way for developers to communicate and discuss the issue directly with our testers through the platform.
This could be especially useful when critical issues are discovered on live systems. The faster a security flaw is fixed, the less likely it is to be exploited by malicious actors. This minimizes potential damage and reduces the risk of data breaches or system compromise.
In the future, we would also like to include more features in the new reporting application. Stuff like “requesting a new penetration test” or “requesting a retest on one specific issue” should be possible through the reporting tool. This could make the workflow from start to finish a lot smoother and we should see an increase in issues being flagged as “fixed” issues sooner. This helps our customers get a clear view of their applications and the evolution of their security.
In conclusion, we feel that the timing is perfect for ushering in an innovative change to our reporting and penetration testing workflow. This transformation holds the promise of enhancing your penetration testing experience significantly, providing you with a far more comprehensive and insightful view of your systems’ security landscape.
Frequently Asked Questions
Before each penetration test, we start with a personal introductory meeting with all key stakeholders. In this session, we outline the scope and discuss the approach for performing a penetration test on the customer’s systems. The test only delivers real value when it’s aligned with the customer’s context and requirements. Once all details are finalized, the penetration test is performed within the agreed timeframe.
Following the test, a review meeting is held to present the identified vulnerabilities along with recommended solutions. A comprehensive report is also provided. More information about our online platform, where customers can log in to monitor and evaluate the security of their applications in real time during testing? New Penetration Test Reporting for Real-Time Insight
With our real-time insight feature, you don’t have to wait until the end of the test. As our testers work, each finding goes through a short internal quality check before being shared. Once validated, it’s immediately pushed to you through our online platform allowing you to track them and take early action — even before the final report is delivered.
Want to learn more about how our platform lets you monitor and evaluate your application’s security in real time during testing? Discover our blog about our Penetration Test Reporting with Real-Time Insight
Web application penetration testing focuses on identifying security vulnerabilities in web-based applications, such as login forms, user inputs, APIs, and session management. It targets application-specific risks like SQL injection, cross-site scripting (XSS), broken authentication, and insecure configurations. The goal is to uncover flaws that could be exploited through the web interface.
Network penetration testing, on the other hand, assesses the security of the underlying network infrastructure, such as servers, routers, switches, and firewalls. It can be conducted externally (from outside the organization) or internally (from within the network) and focuses on vulnerabilities like open ports, outdated software, misconfigurations, and weak credentials.
In short: web app testing targets the software layer, while network testing targets the infrastructure layer.
External penetration testing simulates an attack from outside your organization’s network, typically over the internet. It focuses on publicly accessible systems such as web applications, email servers, firewalls, or VPNs, assessing how vulnerable they are to external threats like hackers or malicious bots.
Internal penetration testing, on the other hand, simulates an attack from within your network, such as from a compromised employee device or a malicious insider. It evaluates what an attacker could access if they bypassed external defenses or had internal access, focusing on internal systems, network segmentation, and privilege escalation. TSF never requests credentials for this type of test and always performs the assessment without initial access to accounts.
Together, both approaches provide a comprehensive view of your organization’s security posture
The ideal frequency for penetration testing depends on your industry, the sensitivity of your data, and how attractive your systems are to potential attackers.
For organizations handling highly sensitive information, such as financial services, healthcare, or government agencies, it’s recommended to conduct penetration tests multiple times per year. This helps ensure you’re staying ahead of evolving attack methods.
For companies in less sensitive sectors, penetration tests should still be performed regularly, especially after significant changes, such as launching a new application version, adding key features, making major infrastructure changes (e.g. new firewalls, cloud migrations), or reorganizing your network.
Penetration testing isn’t just about identifying technical vulnerabilities. It’s also a valuable way to assess how well internal teams, like IT, development, and security, are working together to maintain a secure environment. It should be viewed not as a one-time event, but as an ongoing best practice integrated into your security strategy.
In short, test regularly, and always test when something significant changes.
A security (vulnerability) scan is an automated process that identifies known vulnerabilities in your systems. It provides a broad overview of potential issues, such as outdated software, misconfigurations, or exposed services, by comparing your environment against a database of known threats. It’s a great first layer of defense and is useful for routine checks. However, it typically does not confirm whether those vulnerabilities can actually be exploited or what their real-world impact might be.
In contrast, a penetration test (or pentest) is a manual and semi-automated security assessment conducted by skilled professionals. Testers simulate real-world attacks, actively exploiting vulnerabilities to understand their impact, uncover logic flaws or complex attack paths that scanners can’t detect, and provide detailed insight into the actual risks your organization faces. Every pentest is customized to your systems and business logic.
In short:
- Security scan = fast, automated, wide coverage, high-level results
- Penetration test = slower, manual, deep analysis, actionable risk assessment
External Penetration Testing
Simulates an attack from outside the organization, targeting publicly accessible assets like websites, mail servers, and firewalls.
Internal Penetration Testing
Mimics an attack from within the network, such as by a malicious employee or someone with internal access, to test what can be done once the perimeter is breached.
Cloud Penetration Testing
Targets cloud-based infrastructure (AWS, Azure, Google Cloud, etc.) to identify misconfigurations, insecure interfaces, and weaknesses in cloud-specific services.
Web Application Penetration Testing
Focuses on identifying security flaws in web-based applications, including issues like SQL injection, cross-site scripting (XSS), broken authentication, and insecure APIs.
Mobile Application Penetration Testing
Focuses on mobile apps (iOS, Android) and their interaction with backend services, checking for insecure storage, weak authentication, and data leakage.
API Testing
Focuses on evaluating the security of application programming interfaces (APIs). The test checks for common vulnerabilities such as improper authentication, lack of encryption, and insufficient access controls. It ensures that APIs are securely handling sensitive data and preventing unauthorized access.
Fat/Thick Client Testing
Focuses on security assessments of desktop applications that are installed on end-user devices. These applications often interact with backend systems and store sensitive data locally. The test evaluates risks such as weak encryption, insecure data storage, or potential vulnerabilities in client-server communication.
Kiosk Breakout Testing
Tests the security of self-service kiosks (e.g., in retail or public spaces) to see if an attacker can break out of the kiosk’s restricted environment. The test evaluates the risk of unauthorized access to the underlying system or network, which could lead to data theft or malware installation.
Wireless Penetration Testing
Tests the security of wireless networks (Wi-Fi), including encryption protocols, rogue access points, and wireless client vulnerabilities.
Digital Social Engineering
Evaluates the human element of security, often through phishing or pretexting to determine how susceptible employees are to manipulation.
Physical Social Engineering
Assesses physical security by attempting to gain unauthorized access to buildings, data centers, or secure areas.This type of test often includes a health check, where we look for common physical security issues—such as passwords on post-its, unlocked devices, or unattended access badges.
USB Drop Test
Simulates a scenario where malicious USB devices are dropped in public or accessible areas, such as office spaces or parking lots. The test evaluates whether employees are likely to plug in these devices, potentially giving attackers unauthorized access to the network or introducing malware.
Red Team Testing
A full-scope, multi-layered simulation of a real-world attack that combines many of the above techniques over a longer period to test an organization’s detection and response capabilities.
Absolutely. You can schedule a call with one of our advisers, who will review your specific requirements and provide a customized pricing proposal based on your needs.