The IT security industry is evolving constantly, and as an immediate result of those changes, your security posture is also constantly changing. A single-shot penetration test allows you to have a view on how resilient your application or network is against a cyber-attack, but in the next development cycle or pushed update, a new vulnerability can appear. A pentest is a snapshot… in the current timeframe, the current setup/codebase and currently known vulnerabilities.
Presume that your code is not vulnerable for one type of attack because your framework or Web Application Firewall (WAF) is protecting you. It is highly likely that in the near future a bug is found in your development framework or a WAF bypass is detected which exposes your application anyway.
That’s why continuous penetration testing is important.
Continuous testing makes it possible to detect and improve security at an earlier stage. For example, if one type of vulnerability is present in your entire environment, constantly popping up (even some time after mitigation rounds), that is a clear indication that focus needs to be placed on the development teams. This could be more insights/training in secure coding practices, additional tooling to help and detect these coding flaws, etc. This ensures more qualitative end results, less costs in mitigation and less risk of being hacked.
So when, or how often must penetration testing occur?
The most blunt answer would be: as often as possible. However pentesting comes with a cost. So here are some basic rules to help you make decide:
- New application
- Major updates – new functionalities
- Changes in sensitive data/fucntions e.g. financial transactions
- Yearly, if none of the above applied. Why? Because of newly discovered vulnerabilities in frameworks and the newly discovered hacking techniques

What about retesting?
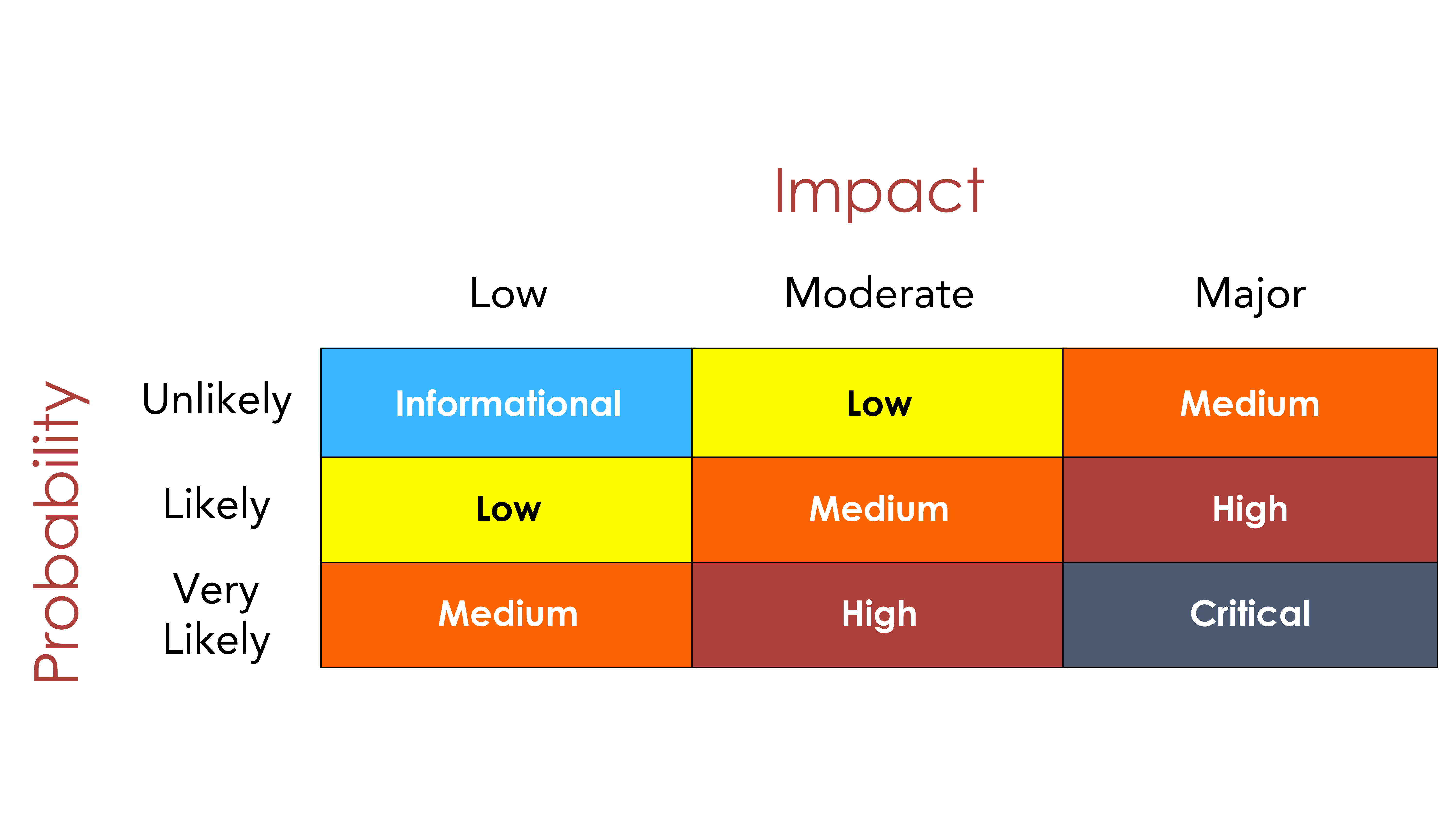
Retesting is also something that is often misinterpreted. One performs a pentest, implements remediations, but never validates if they are adequate. But do you need to mitigate and retest all findings? We typically advise to focus on critical and high rated vulnerabilities. Medium-valued vulnerabilities are open for discussion between security and functional business needs. Vulnerabilities are typically rated in a matrix between probability that the vulnerabilities is exploited and the impact when it happens.
At tSF, we offer the possibility to request retests for specific issues only to ensure budget friendly solutions.
