Phishing is a cyber attack method where criminals impersonate trusted entities (such as banks, delivery services, or even colleagues) to trick recipients into sharing sensitive information. Typically, phishing attempts come via:
Phished’s Security Awareness Training in your organization: the road to success
What is Phishing?
Email phishing
Spear phishing
Business Email Compromise
Smishing & Vishing
Clone phishing
The goal? To steal credentials, financial details, or gain access to systems for further attacks. Phishing is effective because it exploits human psychology: urgency, fear, and trust. Even the best spam filters cannot catch every phishing attempt, making employee awareness crucial.
The human factor in cybersecurity
Companies keep investing in spam filters and technical defenses to block cyberattacks. Yet many threats still slip through and land in employees’ inboxes. That’s where the real risk lies: human error remains the leading cause of cyber incidents.
This makes it essential to prepare employees for the wide range of threats they inevitably face. Phishing simulations are only part of the answer – what’s needed is frequent, relevant training that keeps security top of mind. Too often, awareness programs are too generic or too infrequent to make a lasting impact.
Organizations need a smarter, more engaging approach – one that drives true behavioral change.
The holistic approach to behavioral change
No generic phishing templates. No endless libraries that force IT teams to pick and choose. Instead, Phished offers an approach tailored to your company – fully automated.
By combining AI-driven phishing simulations with the Phished Academy, employees follow a comprehensive, science-based learning path. The outcome: measurable behavioral change that reduces the risk of incidents caused by human error to zero.
With Phished, organizations can:
Assess how employees react to real-world phishing attempts
Strengthen overall security awareness through personalized, automated training
Reduce the risk of data breaches linked to human vulnerabilities
How Phished works
Automated phishing simulations with nanolearnings
AI-driven simulations adapt to each employee’s language, role, context, and skill level. Misclicks are followed by a short nanolearning, so employees learn in the moment – constructively, without blame or embarrassment.
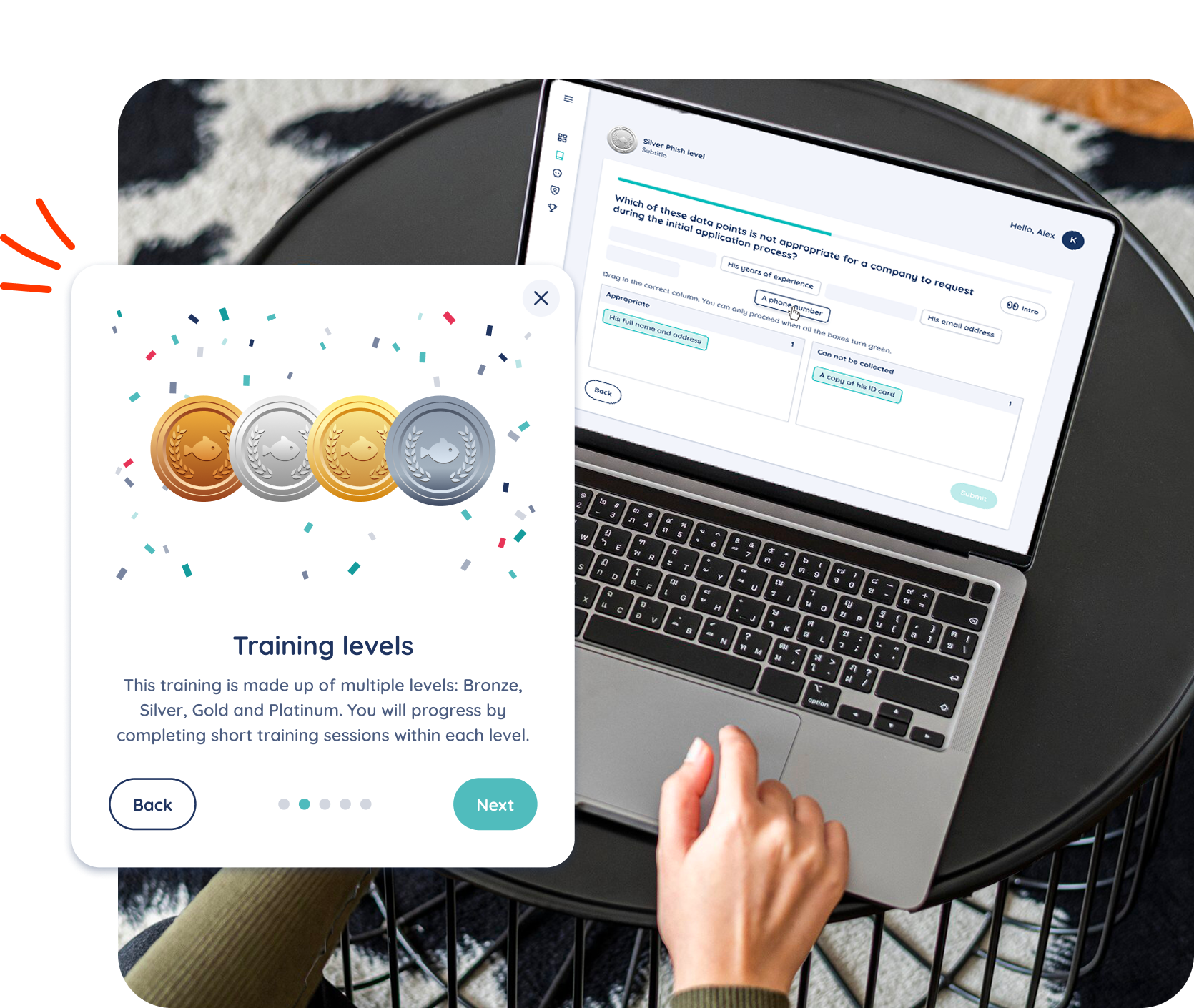
Interactive training curriculum
Employees progress through a structured, science-based curriculum, earning certificates from Bronze to Platinum. Each level includes short, interactive sessions on practical topics ranging from social engineering and financial fraud to AI literacy and remote work.
Specialized training tracks
Tailored training tracks for different departments and roles, with modules on NIS2, GDPR, ISO 27001, SOC 2, and more – so every team has the knowledge needed to meet compliance requirements and apply best practices.
Real-time threat alerts
Short, actionable newsflashes keep employees updated on the latest threats and cyber gang tactics, paired with clear “what-to-do” guidance.
Cyber hygiene practices
Step-by-step guidance on securing commonly used apps and devices, both professional and personal, with practical tips and tricks employees can apply immediately.
Behavioral Risk Score™
A powerful metric that shows administrators exactly how vulnerable their workforce is to phishing attacks – based on simulations clicks and training progress. It highlights awareness gaps, tracks progress, and makes risk reduction measurable.
Risk reporting
Clear, data-driven reporting allows security and management teams to monitor performance, demonstrate compliance, and continuously improve their organization’s security posture.
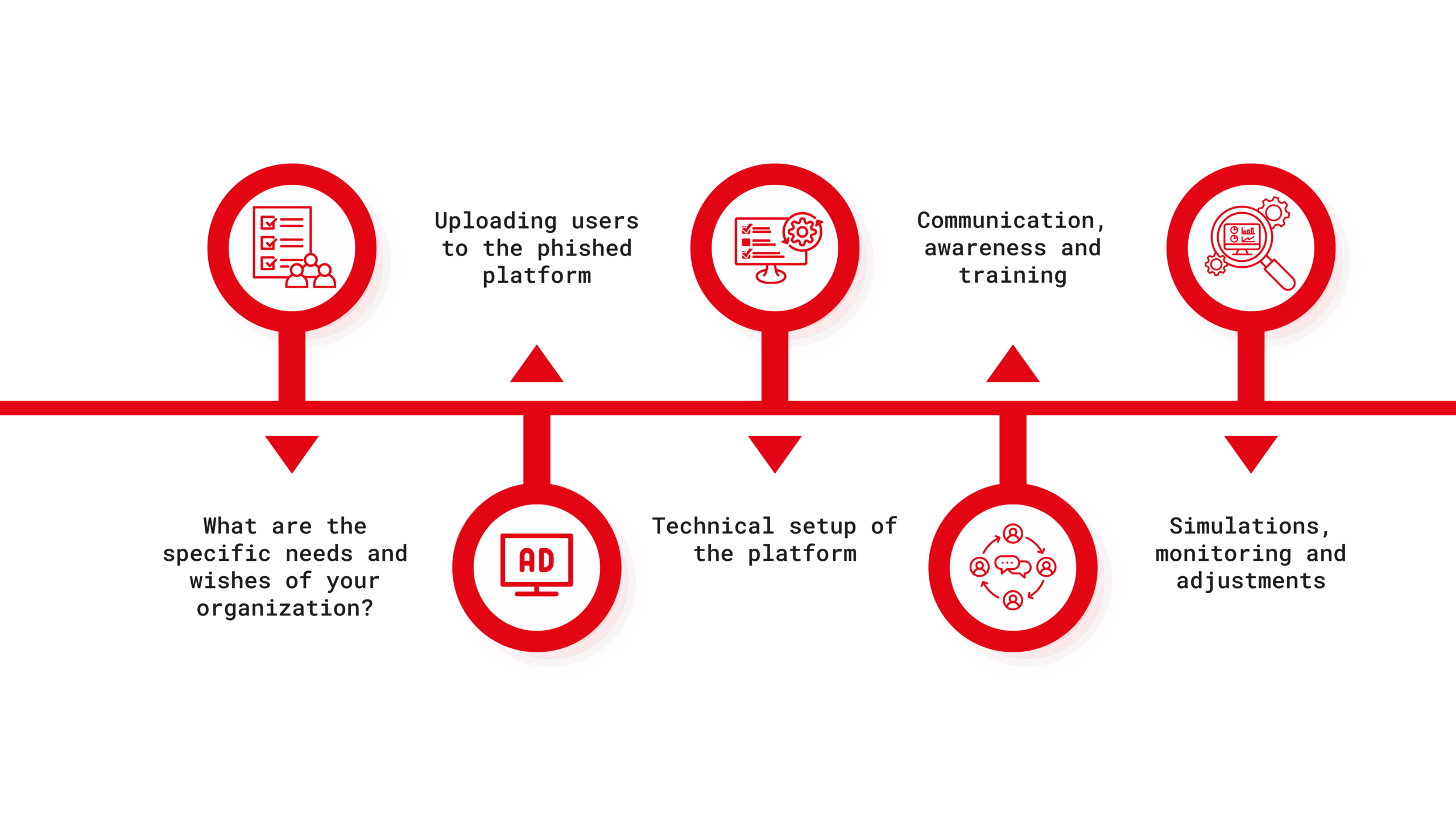

Don’t worry about implementation.
We’ve got your covered!
Our team takes care of the entire Phished implementation process for you. From start to finish, setup is fully managed by us.
We handle setup and configuration so your organization can be up and running the very same day. From then on, everything runs automatically: campaigns are launched, results are collected, and follow-ups are triggered – without requiring time or effort from your IT team.